THINK SAFE. THINK ICS.
Secure Operations
Control, security and transparency for your IT landscape

Secure operation starts with trust
And trust starts with visibility and integrity.
Critical infrastructures, rail systems, logistics networks, energy suppliers or automotive production - when your operational processes are at a standstill, more is at stake than just time: human lives, security of supply, delivery capability and reputation are at stake.
Within historically evolved IT and OT structures, traditional security approaches quickly reach their limits. Heterogeneous systems, distributed locations and increasingly sophisticated attacks require a new level of protection mechanisms. Our answer: holistic, secure operational management - tailored to your requirements. For highly available, resilient and legally compliant systems that also function under pressure.
Your challenges, our solutions
What may seem complex at first glance can be solved sustainably with a structured security approach.
Legal requirements & standards
We help you with the implementation and verification of the following standards:
- §8a BSIG / IT Security Act
- KRITIS Regulation & NIS2 Directive
- ISO 27001 / IEC 62443
- BSI basic protection
Complex, heterogeneous IT/OT landscapes
On-premise, cloud, OT? We connect everything - securely, quickly and in compliance with standards. We rely on modular architectures and end-to-end interface compatibility, regardless of manufacturer or age.
Safety is not lived in the company
If specifications do not work on a day-to-day basis, security remains a theory. We align security processes with your day-to-day business - clearly structured, pragmatically implemented and without unnecessary hurdles.
Lack of automation & integration into existing processes
Efficient security processes need automation. We integrate our solutions seamlessly into your existing SIEM, CMDB or EDR landscapes.
Alert fatigue due to irrelevant alerts
Weuse expert-based prioritization to separate the important from the unimportant. So that your analysts can work efficiently and purposefully.
Data protection & supply chain risks
We rely on GDPR-compliant data handling, DEKRA-certified processes and superior IT security. Made in Germany.
Systems not hardened throughout
Unhardened systems offer unnecessary attack surfaces. We support you in technical hardening with coordinated measures, guidelines and realistic implementation paths.
Blue teaming without structure and depth
Reactive defense is not enough. We work with you to develop structured blue teaming with clear roles, coordinated use cases and practical processes for real resilience.
SOC is missing or does not function holistically
A Security Operations Center must do more than just raise the alarm. We support you in setting up or optimizing it - modular, scalable and tailored to your resources.
Log data without a strategy or target image
Without a sensible logging strategy, security remains blind. We help you to identify relevant data sources, record log streams in a structured manner and evaluate them in a targeted manner.
Detection use cases without effect
Standard rules do not detect targeted attacks. We work with you to develop use cases that really suit your environment. Specific, prioritized and traceable in operation.
No clear responsibilities in security operations
Who responds in an emergency - and how quickly? We work with you to define clear roles, decision paths and processes so that security incidents do not get bogged down in a vacuum of responsibility.
Onboarding takes too long? Not with us.
Thanks to proven frameworks and tried-and-tested processes, you can get started quickly. With a secure setup and clearly defined handovers.
Lack of transparency
We provide a holistic security view across your entire infrastructure. With intelligentanalysesthat can centrally recorddata flows, user behaviour and system statuses and analyze risks.
Unclear or volume-based cost models
Our price structure is predictable, transparent and geared to your actual needs, with no nasty surprises.

Tip: Security with a system
How secure is your business right now?
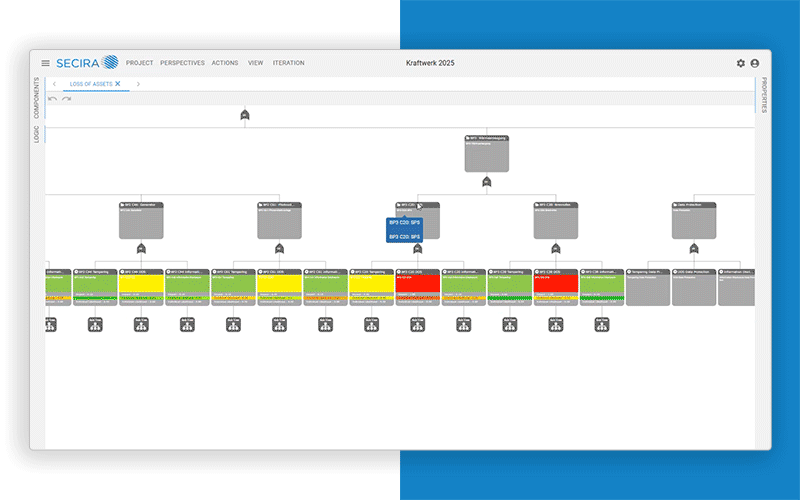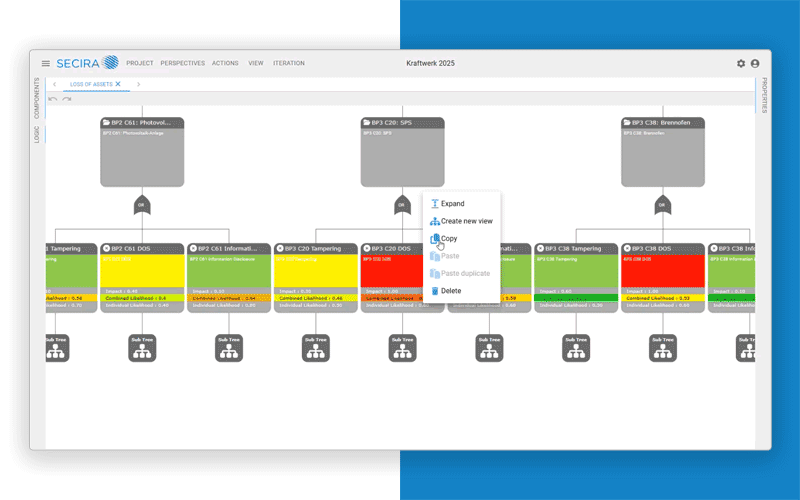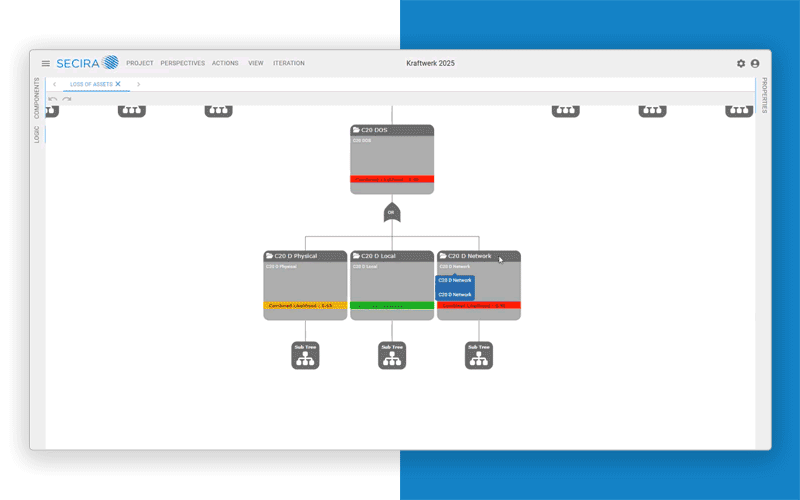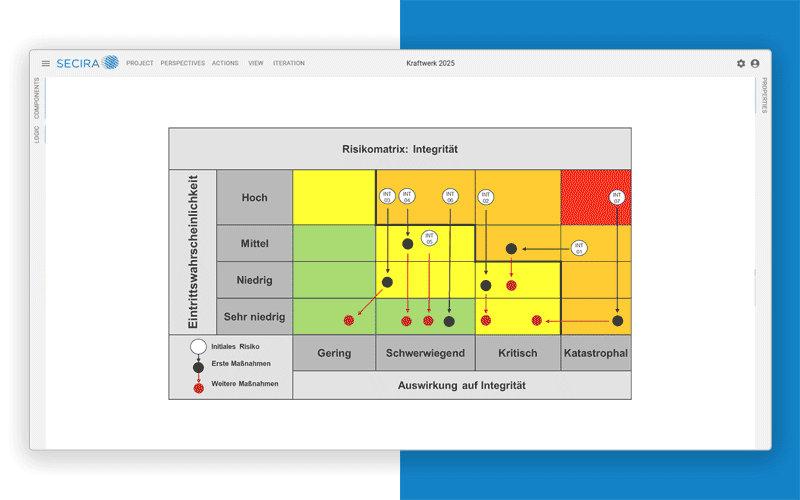
With SECIRA our risk management tool, you receive daily updated insights into your security situation - transparent, comprehensible and immediately actionable. With anomaly detection and automated monitoring on request, so that you not only see risks, but are always one step ahead of them.
What ICS makes possible for you
You keep your business running - we make sure that security doesn't get in the way, but runs reliably with it. Tailored to your processes, requirements and goals.
Compliance built-in
Whether hospital, railroad line, production line or energy distributor: We know your regulatory obligations and support you with audits and certifications.
Incident response & business continuity
With clearly defined escalation paths, regular exercises and coordinated recovery processes, you remain capable of acting at all times.
Monitoring with SECIRA - developed for Critical Infrastructure & Co.
Our holistic risk management tool SECIRA is your central platform for monitoring your risks.
Holistic risk assessment & management
From vulnerability analysis to planning protective measures. Including documentation and attack tree analysis with SECIRA.
Lifecycle security
Protection of your systems over the entire lifecycle.
PKI integration by design
For trustworthy, scalable security infrastructures.
Security-as-a-Service
With SOC, SIEM, Incident Response, CISOaaS.
Personal advice
Short distances, familiar faces. We accompany you reliably and directly.
Protecting digital identities - with PKI
Public Key Infrastructure (PKI)secures digital identities, enables the implementation of encrypted communication and thus authentication at the highest level. Whether users, devices or services: with our individual PKIsolution, we create trust in every connection - automated, scalable and compliant. PKI thus forms the basis for zero trust architectures and protects against identity theft, spoofing and manipulation.
Why ICS?
You know your processes and we bring the security know-how to them. For around 60 years, we have been supporting companies in security-critical industries with practical advice, standard-compliant procedures and technologies such as SECIRA and PKI. From analysis to secure operation: we think along with you, listen and deliver solutions that suit you.

FAQ - Frequently asked questions
What is Secure Operations?
Secure Operations stands for the continuous, proactive protection of IT and OT systems during ongoing operations. The aim is to identify security risks at an early stage, manage them systematically and ensure the long-term functionality of critical processes - technically, organizationally and in compliance with standards.
How do secure operations differ from traditional IT security measures?
While traditional measures are often reactive and selective (e.g. firewalls, audits), secure operations are permanent processes for monitoring, responding and improving. They combine monitoring, incident response, risk assessment and compliance capability in a holistic operational approach - tailored to highly critical infrastructures.
Why are secure operations particularly important for Critical Infrastructure and industrial companies?
Because they operate in an environment in which availability equals system relevance. A failure here can cause not only economic but also social damage. Secure operations help to fulfilllegal obligations (e.g. §8a BSIG, NIS2), ensure operational capability and close security gaps in a structured manner.
What is typically part of a secure operations concept?
A comprehensive concept includes
- Analysis & evaluation of security risks in operation
- Definition and implementation of suitable monitoring mechanisms
- Establishment of incident response processes
- Regular review and optimization of the security situation
- Training and awareness measures for persons involved
- Documentation to provide evidence to third parties (e.g. auditors )
What are typical triggers for the introduction of Secure Operations?
Answer:
- New legal requirements (e.g. NIS2, IT-SiG 2.0 )
- Audits or external audits
- Internal security incidents or near misses
- Digitalization or modernization of OT systems
- Cloud/hybrid architecture or Industry 4. 0 projects
- Customer specifications in sectors such as automotive, rail, energy or logistics
How does Secure Operations affect existing operational processes?
When implemented correctly, secure operationsdo notdisrupt your processes , but make them more robust and easier to control. Security measures are embedded in existing processes - e.g. via automated alerts, clearly defined escalation routines or coordinated maintenance windows.
How do you ensure that Secure Operations remains up-to-date?
Through regular risk analyses, incident reviews, updates to attack detection and the inclusion of new regulatory requirements. Secure Operations is not a one-off project, but a living process that we maintain and develop together with you.
Act now - before others do.
Let's transform your IT security together.
We'll show you how to regain control and secure your digital futurewith secure operations and integrated PKI.